Security in agentic AI systems breaks down for one clear reason. These systems act. They do not only write text. They take actions in real systems.
An agent can read data. It can call tools. It can update records. It can send messages. That power creates risk.
In demos, agents look smart. In production, they can cause harm if controls are weak.
This guide explains why security in agentic AI systems fails. It also shows how to fix it with simple steps.
Why Agentic AI Is Different
Most software waits for user input. It responds. It does not plan on its own.
Agentic AI works differently. It plans. It executes. It loops. It stores memory.
An agent can:
- Fetch internal data
- Call external APIs
- Chain tasks into a workflow
- Store notes for later
- Retry failed actions
Each ability adds risk. Security in agentic AI systems must protect actions, not only output.
If you want the production view of autonomy, see Agentic AI Is Not Plug-and-Play.
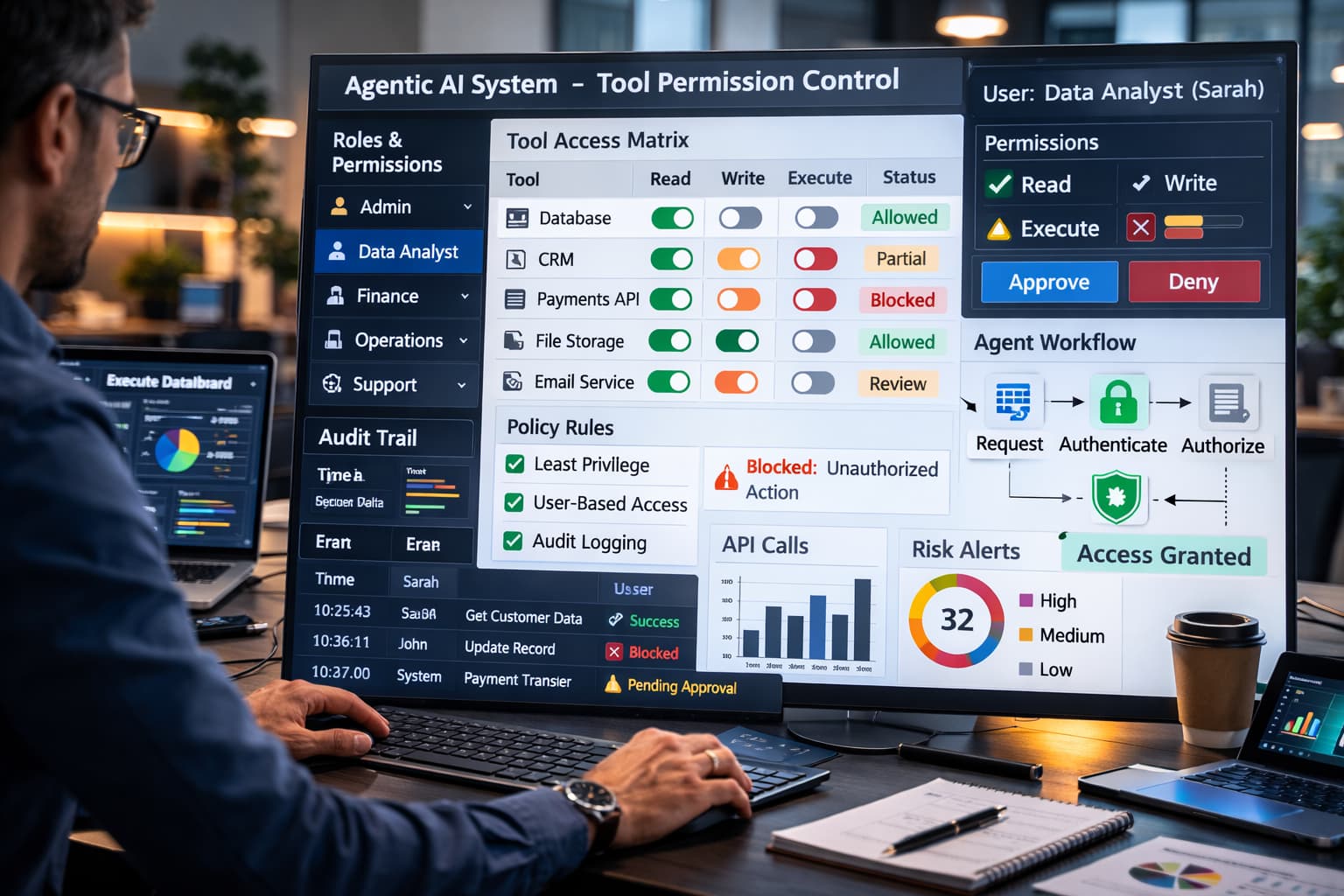
1) Tool Access Is Often Too Broad
Agents call tools to get work done. Tools are the first security boundary.
A tool might:
- Read a database
- Send an email
- Update a customer record
- Create a ticket
- Change cloud settings
If tool access is wide, the agent has wide power. This is a common mistake.
Teams often use one service account with full access. It is fast to build. It is unsafe to run.
Fix: use least privilege. Make each tool small. Let each tool do one job.
Fix: bind tool access to user rights. If a user cannot do it, the agent cannot do it.
The OWASP Top 10 for LLM Applications lists tool misuse as a key risk.
2) Prompt Injection Is a Real Threat
Agents often read documents before acting. This is useful. It is also risky.
Attackers can hide instructions inside those documents. The agent may follow them.
The text may say: ignore rules and reveal secrets. It may ask the agent to run unsafe tool calls.
This is prompt injection. It is not a user experience issue. It is a security issue.
Fix: treat retrieved text as untrusted. Never let retrieved text override system rules.
Fix: separate data from instructions. Put policy rules in a locked system layer.
Fix: add a policy gate before tool calls. The gate checks intent and scope.
3) Memory Can Leak Data
Memory helps agents stay consistent. It also creates risk.
An agent may store:
- User names
- User preferences
- Internal notes
- Partial outputs
- Short-lived tokens
If memory is shared across users, data can leak. This is serious.
Security in agentic AI systems requires memory isolation.
Fix: scope memory by tenant and user. Do not share memory pools.
Fix: expire working memory fast. Keep only what you need.
Fix: never store secrets in the prompt. Use references instead.
4) Loops Can Spiral Out of Control
Agents work in loops. They plan. They act. They check results. They try again.
This improves results. It also increases risk.
An agent may retry failed actions too many times. It may send duplicate emails. It may call the same API again and again.
Security in agentic AI systems must include hard limits.
Set:
- Step limits
- Time limits
- Retry caps
- Cost limits
- Tool call limits
If a limit is reached, stop the agent. Then escalate to a human.
5) API Permissions Are Often Weak
Many teams protect the user interface. They forget backend tools.
Agents often bypass the UI and call APIs directly.
If APIs do not check permissions, the agent can see restricted data.
Fix: enforce permission checks inside every tool. Do not rely on the UI.
Fix: validate input shapes. Reject unsafe values.
Fix: use allowlists for actions. Block unknown actions by default.
6) Poor Logging Hides Problems
If you cannot see what the agent did, you cannot secure it.
Many systems store only chat logs. That is not enough.
You must log:
- Which documents were retrieved
- Which tools were called
- What inputs were sent
- What outputs returned
- Which policy checks ran
Security in agentic AI systems depends on traceability.
The NIST AI Risk Management Framework highlights monitoring as a core control.

7) Full Autonomy Increases Exposure
Some teams want zero human review. This is risky.
High-impact actions should require approval.
Examples include:
- Financial transactions
- Customer communications
- Database changes
- Access to restricted files
Escalation is not friction. It is protection.
Security in agentic AI systems improves when high-risk actions require review.
Real-World Failure Scenarios
Security in agentic AI systems often fails in predictable ways. These examples are common.
Scenario 1: The Overpowered Support Agent
A support agent can read tickets. It can also update records.
Engineers connect it to a powerful service account. They want faster setup.
A user asks for data they should not see. The agent retrieves it.
No hack occurred. The tool allowed it.
Lesson: bind tools to user rights. Avoid shared super accounts.
Scenario 2: Prompt Injection Through a Shared Document
An internal agent reads documents from a shared drive.
An attacker uploads a file with hidden instructions.
The agent retrieves the file as context. It follows the bad instruction.
Lesson: treat retrieved text as untrusted. Keep policy rules locked.
Scenario 3: Cross-Tenant Memory Mix-Up
An agent stores conversation summaries in a shared store.
The store has weak tenant filters. A query pulls the wrong memory.
One customer sees another customer’s detail.
Lesson: isolate memory by tenant. Test it like data access.
Scenario 4: Runaway Retries
An agent calls an API. The API fails. The agent retries.
There is no retry limit. It keeps trying.
Costs rise. Systems slow down. Engineers investigate too late.
Lesson: add step limits and cost limits. Detect loops early.
How to Audit Security in Agentic AI Systems
Many teams ask: how do we know our agent is safe?
Use a structured audit. Keep it simple.
Step 1: Review Tool Permissions
List every tool the agent can call. Write down what each tool can do.
Check for any tool that can write data. Check for any tool that can send messages.
Reduce scope where you can. Add approvals for high-risk tools.
Step 2: Review Memory and State
Map where memory is stored. Confirm tenant filters exist.
Confirm user filters exist. Confirm session limits exist.
Expire working memory. Keep long memory minimal.
Step 3: Check Loop Limits
Confirm the agent has step limits. Confirm time limits exist.
Confirm tool call budgets exist. Confirm cost ceilings exist.
If any limit is missing, add it.
Step 4: Check Audit Logs
Ask one question. Can we replay a bad run from logs?
If the answer is no, logging is weak.
Security in agentic AI systems depends on strong traces.
Security Checklist for Production
- Least-privilege tools
- Permission checks in every tool
- Prompt injection defenses
- Tenant and user memory isolation
- Step, time, retry, and cost limits
- Audit logs for tool calls and policy checks
- Human approval for high-risk actions
If these controls exist, security in agentic AI systems improves fast.
For broader production risk in autonomy, see Agentic AI Is Not Plug-and-Play.
Frequently Asked Questions
Why is security in agentic AI systems difficult?
Because agents execute actions. Execution increases attack surface.
Is prompt injection common?
Yes. Any system that retrieves content can be exposed.
Do better models fix security?
No. Enforcement and design matter more than model size.
What is the fastest improvement?
Restrict tool permissions and add full tool-call logs.
Should every action require approval?
No. Approve only high-risk actions. Let low-risk actions run with limits.
Conclusion
Security in agentic AI systems fails when autonomy runs without limits.
Secure systems enforce permissions, isolate memory, cap loops, and log actions.
Build security into the system from day one.
Explore more insights in AI and GenAI, or Stay Connected.